Cybersecurity in Additive Manufacturing: Securing the industry’s future
In the digital world of Additive Manufacturing, just how cybersecure are your operations and your customers' critical parts? A survey of AM producers has suggested that the answer is probably not secure enough. In this article, Auburn University’s Prof Mark Yampolskiy, and industry analyst Joseph Kowen, present a high-altitude overview of the security threats facing those in the AM community. Cybersecurity, they suggest, should be considered as no less important than metallurgy or 'Design for AM' and, with the development of AM-specific standards and third-party security solutions, it need not be an overwhelming task. [First published in Metal AM Vol. 9 No. 4, Winter 2023 | 15 minute read | View on Issuu | Download PDF]

Talk about cybersecurity is everywhere. We worry about cybersecurity in connection to our phones, our home computers and, of course, our work. It’s a ubiquitous topic that is frequently referenced and spoken about across many areas of modern life. Similar to Artificial Intelligence – the other information technology topic that seems to occupy an increasingly central place in personal and professional discourse – cybersecurity is a well-discussed issue in broad terms, but its details are less well understood by many, including professionals in the Additive Manufacturing industry. An analysis of the topic should, therefore, be framed by a clear demarcation of what the security risks mean for the real world of AM, and not merely as an esoteric concern or as a best business practice.
The objective of this article is to act as a high-altitude overview of security threats in AM; a detailed discussion of the strategies for how to mitigate and defend against these threats are best left to a separate article.
In the context of Additive Manufacturing, the value of a debate on the issue of security lies in a feet-on-the-ground understanding of what the term means in practice. To start, let’s describe a couple of scenarios:
Scenario 1
Company A develops an innovative design for a part. It is tested and qualified and is readied for production by AM. Due to a data breach – possibly during the process of transmitting a file to an external service provider – the file is stolen and made available on the web. Company B obtains a copy of the file and can produce the exact part in the original quality without having to shoulder the costs of development or qualification.
Scenario 2
A digital file belonging to Company C is well protected from leakage into the public domain. However, an adversary might have been able to change parameters in the design, or in the build process, resulting in a part that is different in subtle but substantive ways, creating a potential failure in the part with all the downstream risks that such a failure could entail.
These examples are but two of many possible scenarios. While admittedly selecting examples that lean towards the dramatic, they are illustrative of some of the reasons that make cybersecurity an important topic for additive manufacturers.
Cybersecurity experts distinguish between cybersecurity threats and cybersecurity risks, and it is worth pausing briefly on the distinction. A threat is what an adversary could do. A risk is what an adversary would do. In the examples above, both scenarios illustrate threats present in AM, but to assess the risk of each of these, additional company and even part-specific factors are taken into account, such as probability of a successful attack and degree of damage it would cause. Risk assessment is commonly used to prioritise allocation of limited resources, deciding which security threats to address and to what degree.
Tackling selected security threats
![Fig. 2 A generic AM workflow (As published in [2], reproduced with permission)](http://www.metal-am.com/wp-content/uploads/sites/4/2024/01/fig-02-1-1024x629.jpg)
AM can be a complicated process involving many moving parts, all of which are underpinned by data flows. As Fig. 2 shows, generic data and material flow in an AM environment has many components. What then are the main security issues or defensive objectives relevant to the AM world?
Intellectual property protection
Since Additive Manufacturing, by definition, involves producing products from a digital design, if these digital files are not adequately secured, there’s a risk of intellectual property theft. Cybersecurity measures help prevent unauthorised access and protect sensitive design information.
Preventing counterfeiting
Related to intellectual property protection in industries where product authenticity is crucial, such as automotive or aerospace, cybersecurity measures help prevent the unauthorised replication of additively manufactured components. Counterfeit parts, which are often of inferior quality, can compromise safety and performance.
Data integrity
Ensuring the integrity of the digital files used in the Additive Manufacturing process is essential. Any tampering with the digital design files could result in defects in the final product, compromising its quality and functionality.
Production security
Cybersecurity is critical to maintain the integrity of the Additive Manufacturing process itself. Hackers could potentially compromise the Additive Manufacturing process, leading to the production of faulty or substandard products. This is particularly important in industries where safety and reliability are paramount, such as aerospace or medical devices.
Supply chain security
Many industries are increasingly using Additive Manufacturing to create components and parts on demand. Securing the digital supply chain for software and hardware used in AM is crucial to prevent the insertion of malicious code or the manipulation of designs at any stage of the manufacturing process. Protecting the physical supply chain is also critical in an industry dependent upon advanced materials.
Network security
Many AM machines are connected to networks for remote control and in-process monitoring. Ensuring the security of these networks is vital to ensure the quality of parts, prevent unauthorised access, potential sabotage, or the introduction of malware.
Regulatory compliance
In certain industries, such as aerospace and medical, there are strict regulations and standards regarding the security of digital designs and manufacturing processes. Adhering to the AM part-corresponding regulations is not only a legal requirement but also essential for maintaining trust and credibility in the market.
Data types in Additive Manufacturing
As in many areas of our digital world, the volume of digital data surrounding AM has mushroomed. We find data in a wide range of different operations and processes within AM:
Digital design files
The Additive Manufacturing process starts with a digital design file, which determines the geometry for the object to be additively manufactured. Protecting these files is crucial to prevent unauthorised part reproduction or theft of intellectual property.
Build parameters and settings
The parameters and settings used during the Additive Manufacturing process, such as laser power, layer thickness, and material composition, are essential for the quality of the final product. Cybersecurity measures are needed to prevent unauthorised changes to these settings that could lead to defects in the manufactured parts.
Process monitoring data
Many AM machines are equipped with sensors for monitoring the build process in real time. This data is important for quality control and process optimisation. Protecting the veracity and integrity of this data is essential to ensure the reliability and consistency of the manufacturing process. Furthermore, privacy of this data might need to be ensured to protect the ‘secret sauce’ of manufacturing process parameters.
Digital supply chain
The digital supply chain for AM involves the transfer of digital files and software between various stakeholders, including designers, manufacturers, and suppliers. Securing this data is essential to prevent the introduction of malicious code into software or the compromise of design files during the exchange. The digital supply chain also involves the data relevant to procuring and storing materials used in the manufacturing process.
Equipment access control data
This involves authentication mechanisms, user permissions, and secure access protocols to prevent unauthorised individuals from manipulating the process. This also includes changing the default name and password set by the equipment manufacturer.
Testing and quality assurance data
Data generated during testing and quality assurance processes, such as material testing results and inspection reports. In many industries these are essential for traceability and thus need to be protected to comply with industry standards.
Network data
As many AM machines are connected to networks for remote monitoring and control, securing network communication is critical. This includes data transmitted between the AM machine and external systems, as well as the security of the network infrastructure itself.
The Additive Manufacturing cybersecurity disconnect
With the proliferation and growth of AM technologies, it cannot be said that the community is completely unaware of the issue of cybersecurity. After all, AM is a digital manufacturing technology that is squarely based on information technologies in a wide variety of aspects. However, there is a disconnect between an AM community focused on producing physical parts and security professionals – even those active in AM – who are focused on securing this highly digitalised technology.
A study [1] was conducted in 2021 to measure the depth and breadth of cybersecurity awareness among companies engaging in, or contemplating adoption of, AM. The study was conducted through a collaboration between the Department of Computer Science at the University of Auburn, Alabama, USA, and ASTM International, and published by the latter. Survey respondents were members of America Makes.
The survey was designed to poll respondents on their attitudes to cybersecurity in AM, and to measure their understanding of the specific risks associated with their AM activities. They were asked how they and their AM service providers were dealing with data security issues. Key questions posed are listed in Table 1.
![Table 1 Key questions posed in the America Makes cybersecurity survey [1] (partial excerpt of questions posed)](http://www.metal-am.com/wp-content/uploads/sites/4/2024/01/table-01-1-1024x838.jpg)
The findings from the survey make interesting reading. While respondents in general seemed to have knowledge of some key issues in AM security, such as uncontrolled access to intellectual property or data corruption during data transfer from computers to AM machines, the study concluded that most users of AM lack a comprehensive understanding of cybersecurity. In answer to questions on the cybersecurity measures taken by service providers building AM parts, some respondents lacked complete familiarity with cybersecurity terminology and practices. The study concluded that the results indicated confusion regarding the goals that an adversary would hope to derive from an unprotected AM cyber environment.

The study found that 89% of respondents identified theft of technical data as one of their security concerns, and 41% identified the sabotage of parts or equipment as a concern in the manufacturing environment. 84% reported that the objective of the adversarial activity was intelligence gathering, and 41% was for monetary gain. Five respondents – or 9% – (out of fifty-five who answered the question) reported that they had suffered an AM-related cyber incident, though none were willing to share details of the respective incidents. Only 22% of respondents indicated that they had hired or partnered with external AM security providers. A majority of the surveyed organisations (62%) indicated a lack of concern about security issues, having not conducted a risk assessment on the topic. Only 41% of respondents answering the question indicated that they had taken steps to address security threats.

In summary, we can conclude three things. Firstly, there is a general awareness of cybersecurity issues in the AM segment. However, secondly, there is a lack of deeper understanding of the issues and threats involved. And finally, not enough is being done to address the risk.

What’s happening with standards for securing Additive Manufacturing?
A clear outcome from the findings above is that there needs to be a more organised and standardised approach to issues of cybersecurity in the AM segment. At the very least, players in this space need to have a common language and terminology, and a common understanding of the challenges. As in many other areas of standardisation in AM, no one standard will be able to address every concern for all AM processes or businesses. Some standards are developed by organisations in a particular industry vertical who are deeply familiar with the challenges in that space. For example, shipping and maritime standards are being led by testing, insurance and qualification bodies that are already active in the maritime industry. At the very least, general cybersecurity standards for AM would serve the purpose of creating a common baseline around which future efforts, perhaps driven by industry segments, could rally.
Work is already underway to achieve this. Standards relating to security in AM are under development to improve the industry’s posture against threats it is exposed to. Even so, the effort is in its infancy and is a work in process. The Additive Manufacturing Standardisation Collaborative (AMSC), a group sponsored by America Makes and ANSI, published a roadmap in June 2023 to identify gaps in AM standardisation efforts. The relevant parts dealing with data, titled ‘New Gap DA20,’ found that although numerous groups have standardised IT cybersecurity and privacy guidance, and a growing number of standards address Operational Technology (OT) security, no standardised guidance specifically addresses AM security.
On the question of supply chain security, GAP DA21 found that guidance is needed that addresses cyber and non-cyber threats (i.e. side channel attacks) for securing, ordering, maintenance, repair, and replacement parts. This would ensure that ready-to-build 3D models have not been sabotaged and that IP has not been stolen. Secure storage should ensure that only authorised personnel can access files and print parts, the AMSC committee found.
Regarding technical data and IP protection, GAP DA22 declared, “There is currently no standardised method of labelling, securing and authenticating the intellectual property ownership and related rights to AM designs, files and metadata.” This creates a risk for unauthorised use and/or counterfeiting of AM objects. There is no standardised method for authenticating additively manufactured parts against counterfeiting.
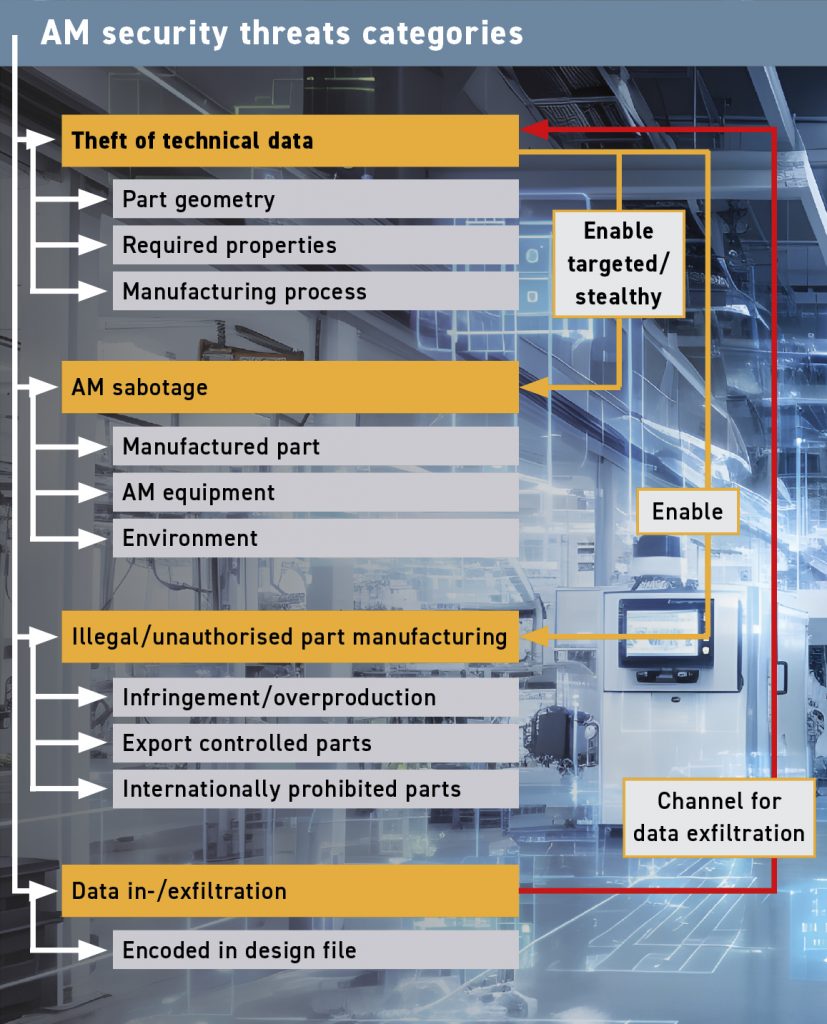
There is currently an effort underway to develop guidelines for AM security. It is called: ‘WK78322 Standard Guide for Additive Manufacturing – General Principles – Guidelines for AM Security.’ This document will establish AM security practices necessary to protect Additive Manufacturing parts’ structural integrity, provenance throughout the production chain, and the protection of technical data. The guide will identify and categorise security threats in AM, highlight characteristic aspects of AM security that require special considerations, and describe mitigations in the manufacturing life cycle.
There is considerable work ahead to develop a more comprehensive regulatory framework for data security in AM, but at least the framework is starting to take shape.
Opportunities for solution providers
In many respects, the area of security for AM is still in its infancy, and – separately from standards – opportunities therefore abound for cybersecurity solution providers to enter the market. These providers can propose products or services that shore up areas where manufacturers and most service providers lack expertise, which, until now, have left AM end-users to fend for themselves. As it is, AM technology providers face enough challenges developing their systems and materials, and they should not be expected to devote efforts to deal with very complex cybersecurity issues. This opens the way for third-party cybersecurity solution developers to offer dedicated tools to mitigate security risks in AM.
For example, Assembrix, based in Israel, has developed a ‘virtual manufacturing’ platform that enables machine operators to control and monitor AM build activity remotely. The cloud-based platform enables a simpler, more efficient, and more secure production process by overseeing the entire AM digital thread, from the initial part model to the verified physical part and beyond. The platform enables multiple in-house users or external clients to monitor, allocate and manage their entire manufacturing space, thereby optimising the utilisation of all Additive Manufacturing resources. The backbone of this solution is a secure data environment. This is made possible through the utilisation of blockchain and encryption technologies.
Assembrix’s approach to implementing this secure environment is to partner with AM machine manufacturers by connecting their machines to the Assembrix platform and providing its customers with full management and control over their operation within a secured and networked system. By collaborating with AM machine manufacturers, Assembrix’s solution can communicate with these machines at a deep machine level, in a secure way.
In May 2023, Assembrix announced a partnership with Nikon SLM Solutions whereby the Assembrix platform was integrated into Nikon SLM Solutions machines. This integration facilitates built-in remote manufacturing possibilities. For example, an operator at a central location can operate and monitor AM systems located remotely.
Earlier, in 2021, Assembrix partnered with Boeing, EOS, 3T Additive Manufacturing, and BEAMIT, and successfully demonstrated secure cross-continent, distributed Additive Manufacturing. The demonstration showed how a controlled build job was remotely and directly connected to EOS AM machines.
Another example is Vistory, a French cybersecurity company focusing on AM. It specialises in cybersecurity software development, particularly for supply chain security. Vistory is now leveraging this expertise to provide a mobile platform for the on-demand production of spare parts. Founded in 2015, the company’s blockchain-supported operating system ensures the confidentiality and integrity of manufacturing data while providing intellectual property protection and traceability of operations. It enables a manufacturer to control the risks of the digital supply chain for secure decentralised production.
The company’s initial focus was offering secure manufacturing for the French armed services. In 2019 the tool was tested and adopted by the French Land Forces. The French army’s maintenance division required Vistory to guarantee suppliers’ intellectual property while allowing the army to additively manufacture spare parts onsite. More recently, the company, in conjunction with hardware manufacturers, developed a container-based manufacturing cell for deployment in military or war time environments. The company’s secure manufacturing operating system forms the basis on which the cell’s AM operations are managed. In October 2023, the company participated in a project to provide the Ukrainian armed services with AM capacity for deployment close to front lines. The company addresses the civil sector, enabling manufacturers to offer their customers new solutions for the production and supply of spare parts while retaining control of their intellectual property and manufacturing processes.
Insights
No system is 100% secure, cybersecurity experts are quick to point out. A greater awareness of the risks, however, is the first step in shaping an approach that strives to achieve as close to 100% as is possible in the circumstances. Identification of cyber risks is, therefore, a critical first step in ensuring that AM remains as secure as it can be.
Once risks have been identified, organisations would be wise to understand the economic or strategic meaning of that risk for their business. In this regard, corporate management, risk managers or business owners can best evaluate what the meaning of a data breach is for their businesses. This will differ per industry, by company size, and by risk profile including parts manufactured and what they are used for, among other factors. Most manufacturers know by instinct where the critical path for their business lies. The key is to have as full an understanding as possible of what their exposure to security risks actually is. Manufacturers, including in AM, naturally have better instincts regarding physical risks. For example, an AM facility using titanium powder has a known risk of explosion if the powder is not correctly managed. Without minimising the seriousness of such real-life risks, a cybersecurity risk is the digital equivalent of a reactive powder explosion and may even have a bigger strategic impact on a business than its physical analogue.
Once risks have been assigned an economic value, companies can begin the task of deciding how to mitigate that risk, understanding the costs of that mitigation, and making an informed decision on what kind of investment makes sense to achieve maximum security within available resources. The approach taken must be calibrated for maximum effect wherever it is needed most, and when the cost-benefit trade off makes sense.
Finally, greater cyber protection will provide manufacturers and their customers with the confidence to adopt new business practices and business models that they cannot currently contemplate. The promise of new opportunities supported by cybersecurity solutions will attract innovative companies with cybersecurity experience to offer solutions to manufacturers using AM. Equipped with a new generation of functional digital security tools, manufacturers will be able to entertain new models of business, such as remote manufacturing, digital inventory of parts, on demand spare parts manufacturing, and other solutions that we may not yet fully envision. Paradoxically, as is sometimes the case in life, a threat becomes a catalyst for change and growth. Instead of cybersecurity risks being a cost or tax on the business, innovative solutions inspired by those risks, properly developed by creative and nimble minds, could turn out to be a differentiating factor for new growth.
An axiom of economics and life is that incentives inspire action. As AM grows, it will become a more valuable industry and, by extension, a bigger target for adversarial interests wanting to get a piece of others’ hard-earned success. But just as cyber threats have not stopped the development of online tools, like banking, accounting, and shopping, to name just a few, so too will AM advance and rebuff the challenges facing it on the cyber front.
The promise of digital manufacturing is simply too attractive a growth opportunity, but growing it safely will be paramount. While there is a relatively anaemic level of awareness on cybersecurity in the industry right now, one could say that the nascent regulatory efforts, as well as innovative efforts to develop new tools, constitute a ‘call to action’ for the broader AM community. Raising awareness and answering the call will result in better ways to deal with security threats. This will lead to the opening of new doors as well as the application of AM in new ways, adding developments in data processing to the advances we have become accustomed to seeing in machines, processes and materials. Cybersecurity is in its own way not less important to AM than chemistry, metallurgy and DfAM. A secure environment in which AM can operate will provide fertile ground on which the physical act of building parts in new and exciting ways can thrive.
Authors
Mark Yampolskiy
Mark Yampolskiy is an Associate Professor of Computer Science and Software Engineering at Auburn University. He specialises in cybersecurity issues in Additive Manufacturing and helped organise ASTM International’s working group on Guidelines for Additive Manufacturing Security.
[email protected]
www.eng.auburn.edu/directory/mzy0033.html
Joseph Kowen
Joseph Kowen is an industry analyst and consultant who has been involved in Additive Manufacturing since 1999. He is an Associate Consultant at Wohlers Associates, part of ASTM International’s AM Center of Excellence.
www.linkedin.com/in/joseph-kowen-a5129b3/
References
[1] M. Yampolskiy, P. Bates, M. Seifi, and N. Shamsaei, “State of Security Awareness in the Additive Manufacturing Industry: 2020 Survey,” in Progress in Additive Manufacturing 2021, ed. N. Shamsaei, N. Hrabe, and M. Seifi (West Conshohocken, PA: ASTM International, 2022), 192–212. http://doi.org/10.1520/STP164420210119
[2] M. Yampolskiy, W.E. King, J. Gatlin, S. Belikovetsky, A. Brown, A. Skjellum, and Y. Elovici. “Security of additive manufacturing: Attack taxonomy and survey.” Additive Manufacturing 21
(2018): 431-457.







